Pocket Ark: Making PPE Training Simple, Smart & Actionable
Overview: Natural disasters like Hurricane Harvey revealed the immense vulnerabilities faced by construction workers who participate in post-disaster recovery efforts. These workers often lack adequate training in hazard recognition, Personal Protective Equipment (PPE) usage, and emergency response—putting their health and lives at risk. “Pocket Ark” was developed as an innovative, mobile-first solution aimed at closing this gap through interactive, engaging, and easy-to-access PPE training.
IT Transformation
IT organization are quickly becoming primary drivers of innovation. IT transformation is critical to keep pace in a highly-competitive digital world by creating and operating a high-performance engine that allows you to see a 360-degree view of your customer, and then it enables the customer experience delivery.
Modernize infrastructure
Radiant will work with you to create a precision infrastructure that is simple to deploy and manage, a secure, cloud-enabled foundation that automates processes, increases agility and reduces operational costs.
- Read more about IT Transformation
- Log in to post comments
Accelerating Innovation and Transformation of Legacy Applications
The continuous digital revolution calls upon enterprises to abandon the crumbling, almost ready-to-expire legacy systems and replace them with more agile modular applications and database management systems.
New-world programming is an enterprise norm today that delivers cost-efficiency and faster time-to-value. Modern-day applications provide better support for multi-device compatibility, resource reusability, cross-platform functionality, and seamless integration with other business systems.
Making Your Business Processes Efficient and Reliable with jBPM Migration
In our previous blog, “Enterprise BPM Transformation – Embrace the Change,” we discussed the transformational capacity of BPM and how it helps organizations gain better visibility that translates into higher productivity. Many companies invest in tools like Lucidchart, Visio, Modelio, Pega BPM, ServiceNow BPM, etc., based on their diverse and specific business needs. While each of them has benefits and limitations, we at Radiant highly recommend jBPM.
What is GrandStack - and why should you use it?
GRANDstack is a combination of technologies that combine to enable software developers to build data-intensive, full-stack applications. It is a new generation framework with notable advantages on other such tech stacks, such as the ability to ship apps across platforms much faster, deliver consistent, high-quality UX, ease the transition to microservices and centrally manage and secure entire APIs more seamlessly than alternatives such as the REST (Representational state transfer) method.
Enterprise BPM Transformation - Embrace the change
Business leaders often experience the heat to remain competitive, deliver quality-driven products and services, optimize costs, and improve productivity.
Many of them are leaning on Business Process Management (BPM) software to make their daily operational processes adaptable, agile, efficient, and reliable to remain relevant in a dynamic tech marketplace.
Championing ‘Secure CI-CD’ with DevSecOps using Gitlab Secure
A successful DevOps implementation has two cornerstones, Continuous Integration and Continuous Deployment. Enterprises can reap the bottom-line benefits of an optimized CI/CD pipeline by automating their build, integration, and testing processes. Conventional IT dev processes involve security at the end of the application or software stack. To break down development and delivery process silos and ship software faster and more securely, securing CI/CD workflows has become necessary.
- Scan the application binaries and source code to spot potential vulnerabilities (like harmful code leading to SQL DB injection) before deployment.
- Scan results are collated and presented as a single report.
- Assess vulnerabilities in the GitLab pipeline and manage issues with one click.
Dependency Scanning
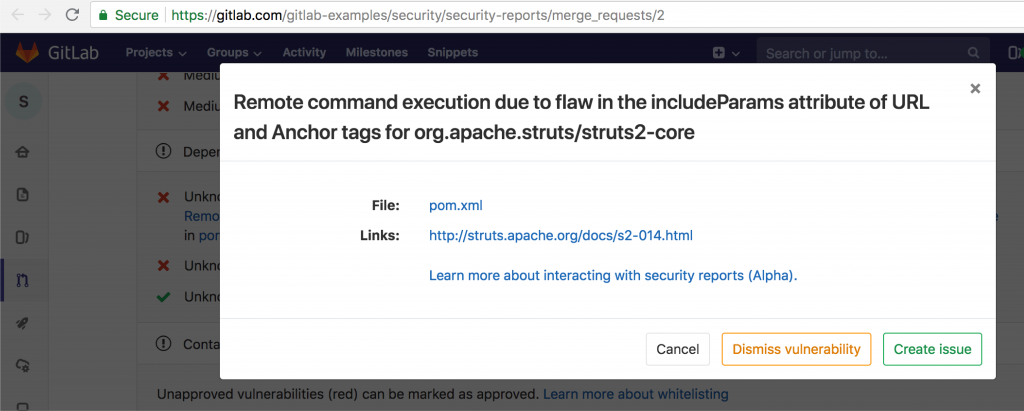
- Analyses external depen
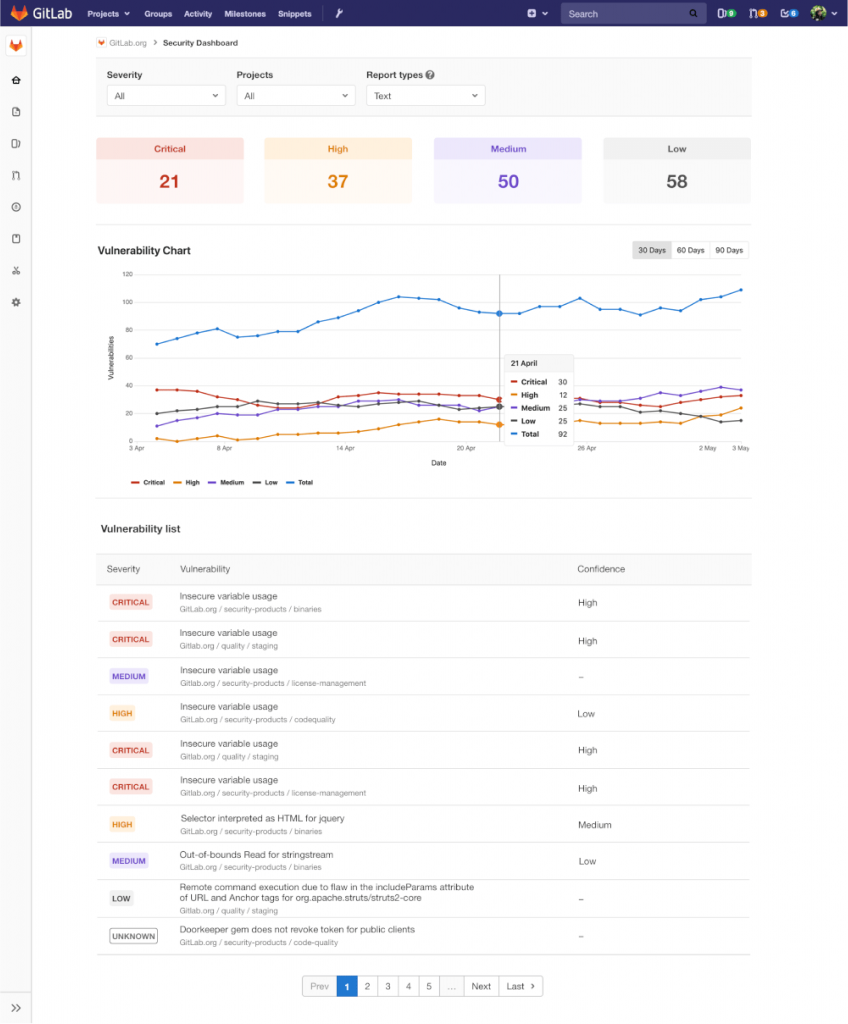
The Security Dashboard is a primary security tool that is available at the group and product levels. It provides an overview of security status and actionable insights to start a remediation process. This tool provides data visualizations for easy consumption of performance information.
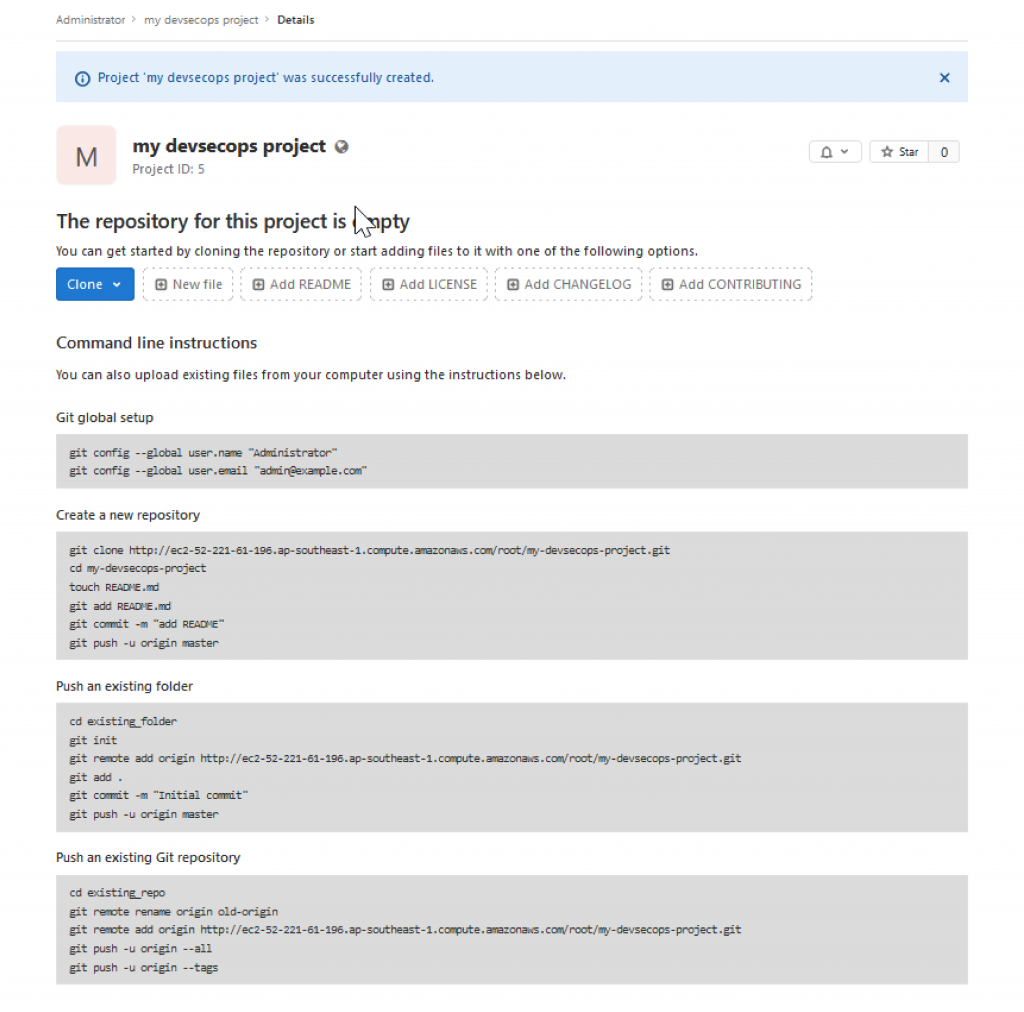
Next, add your source code to this repository using your IDE tools.
Step 2: Add a new .gitlab-ci.yml file for the CI/CD pipeline stages, tasks, etc. GitLab will auto-detect any changes to this file and run your CI/CD pipeline once any changes or updates occur.
Step 3: Set up GitLab Runner to run jobs in the CI/CD pipeline. You can access this Runner at Setting -> CI / CD -> Runner.
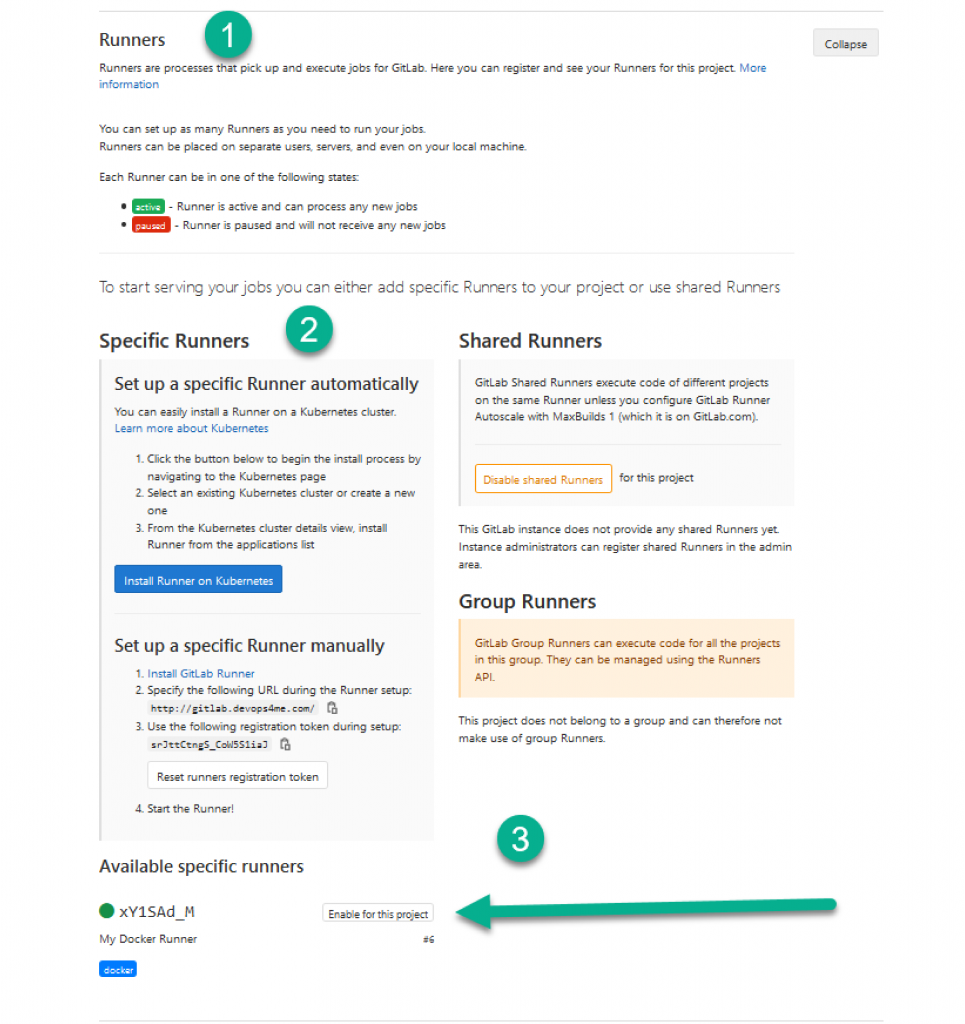
Step 4: Redeploy your CI/CD pipeline by navigating to project -> Pipeline -> Run Pipeline.
Step 5: Next, manually include the security scan templates in the .gitlab-ci.yml file in your existing project.
Step 6: Commit a change and observe your new DevSecOps CI/CD pipeline progress while checking your security and compliance board.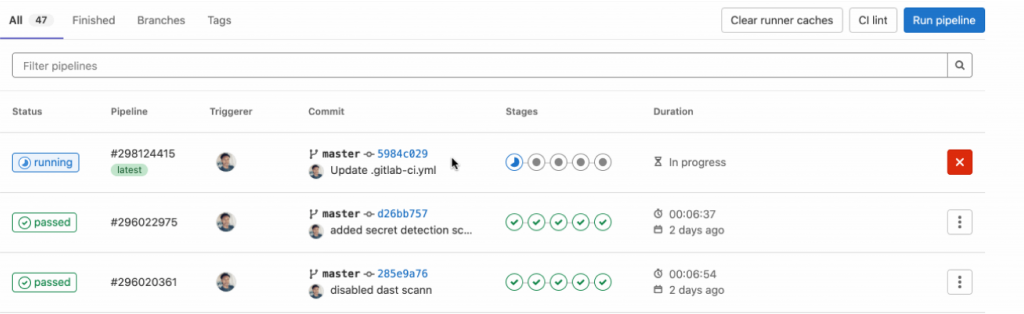
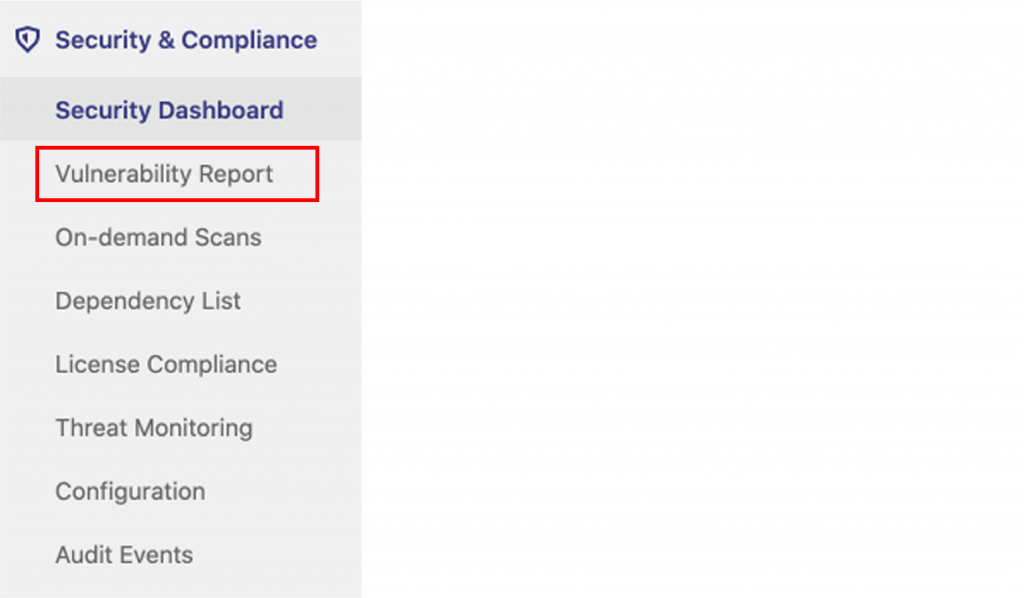
You can view the vulnerability report by clicking on Security & Compliance->Vulnerability Report
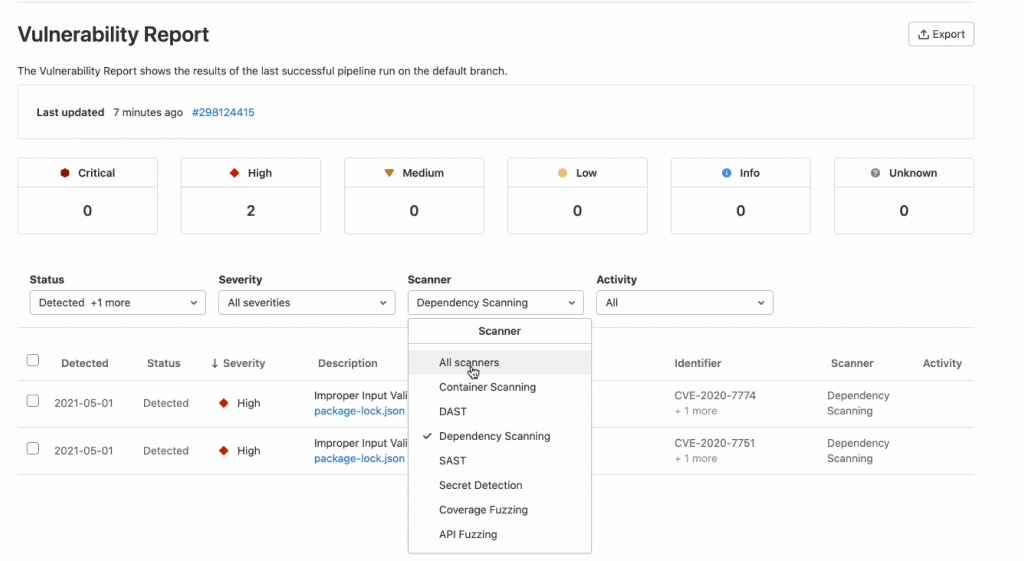
From here, you can keep improvising your app’s security by updating the node js, other docker container package dependencies and modifying your Docker file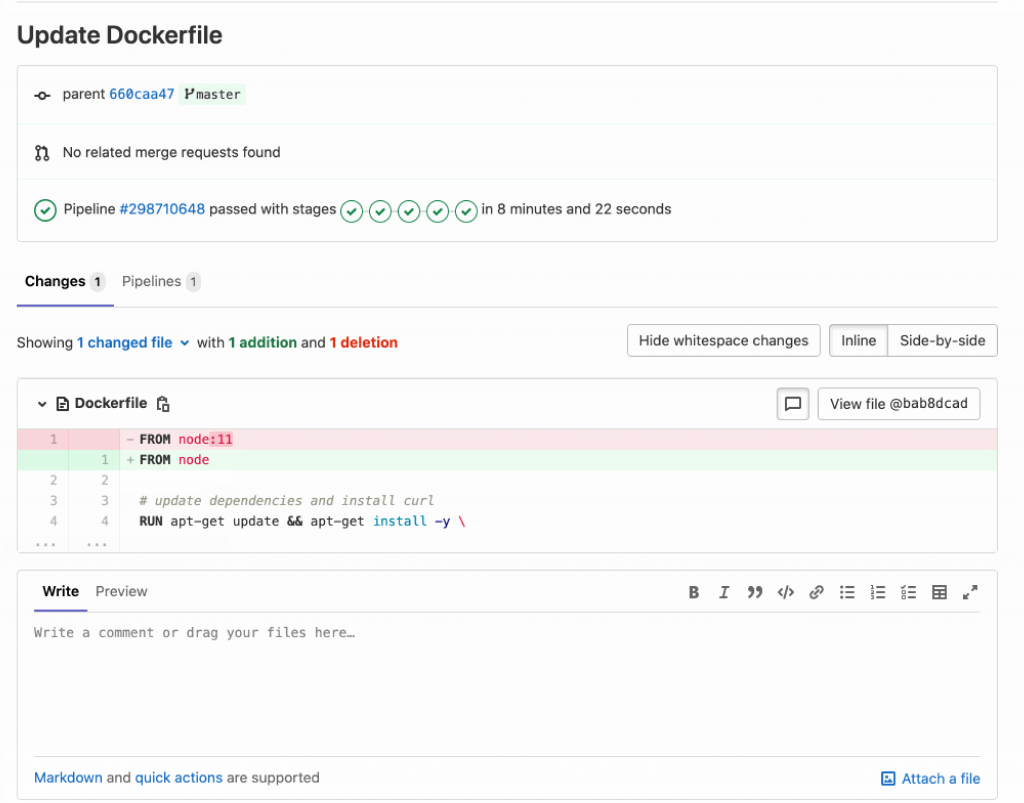
Parting Words
Overall, with DevSecOps available throughout the CI/CD workflow, a single application will help companies improve how they deliver code, reduce release cycles, and innovate. GitLab Secure is a DevSecOps game-changer that applies to governance, construction, verification, and deployment.
© 2025 Radiant Digital. All rights reserved
