A successful DevOps implementation has two cornerstones, Continuous Integration and Continuous Deployment. Enterprises can reap the bottom-line benefits of an optimized CI/CD pipeline by automating their build, integration, and testing processes. Conventional IT dev processes involve security at the end of the application or software stack. To break down development and delivery process silos and ship software faster and more securely, securing CI/CD workflows has become necessary.
- Scan the application binaries and source code to spot potential vulnerabilities (like harmful code leading to SQL DB injection) before deployment.
- Scan results are collated and presented as a single report.
- Assess vulnerabilities in the GitLab pipeline and manage issues with one click.
Dependency Scanning
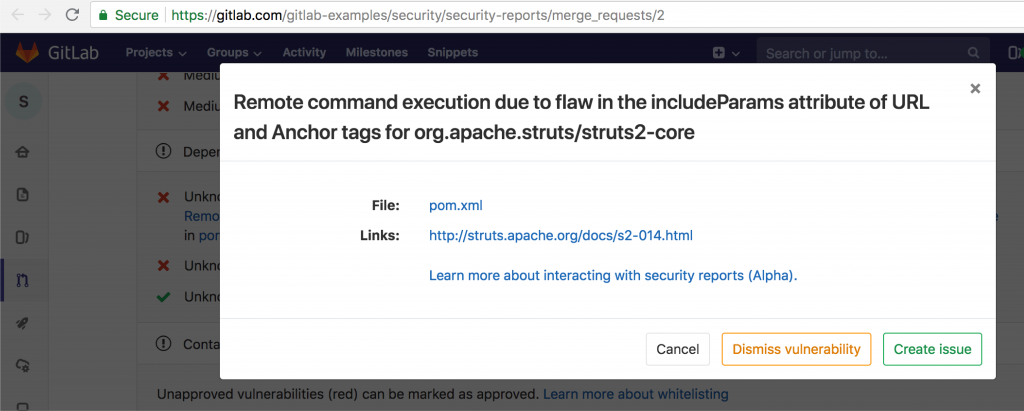
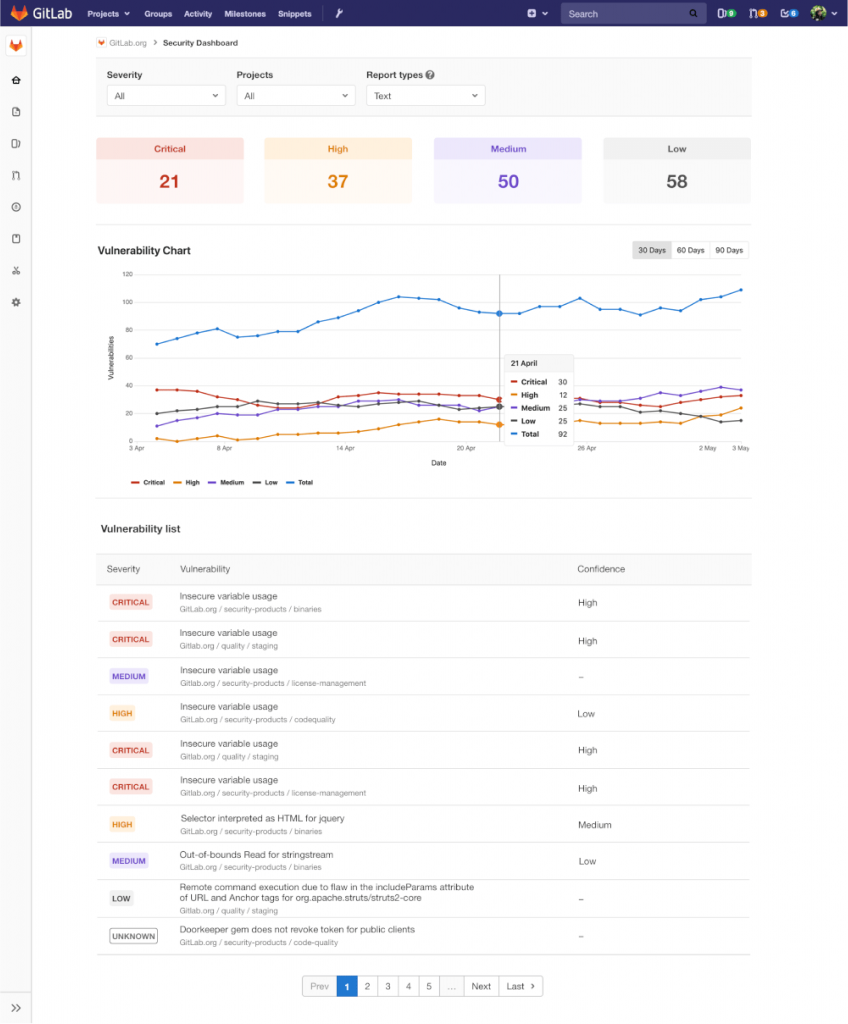
The Security Dashboard is a primary security tool that is available at the group and product levels. It provides an overview of security status and actionable insights to start a remediation process. This tool provides data visualizations for easy consumption of performance information.
Next, add your source code to this repository using your IDE tools.
Step 2: Add a new .gitlab-ci.yml file for the CI/CD pipeline stages, tasks, etc. GitLab will auto-detect any changes to this file and run your CI/CD pipeline once any changes or updates occur.
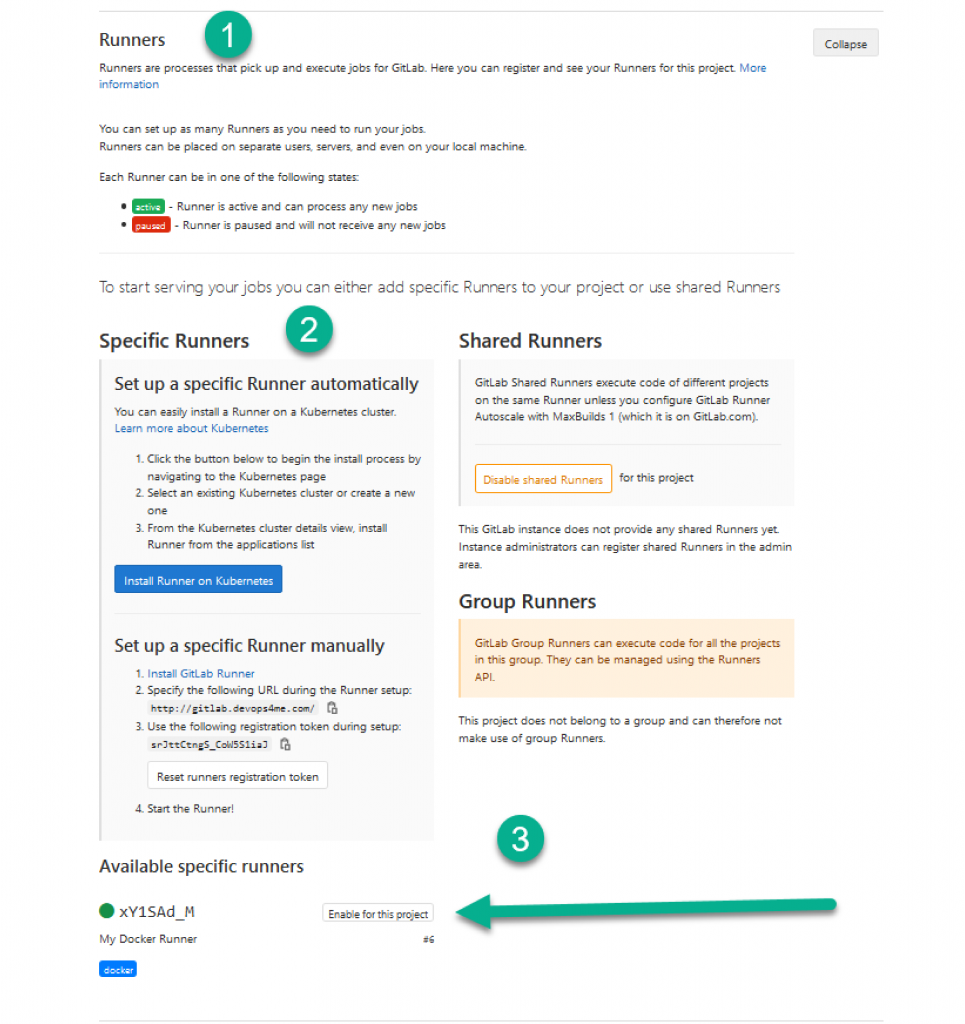
Step 3: Set up GitLab Runner to run jobs in the CI/CD pipeline. You can access this Runner at Setting -> CI / CD -> Runner.
Step 4: Redeploy your CI/CD pipeline by navigating to project -> Pipeline -> Run Pipeline.
Step 5: Next, manually include the security scan templates in the .gitlab-ci.yml file in your existing project.
Step 6: Commit a change and observe your new DevSecOps CI/CD pipeline progress while checking your security and compliance board.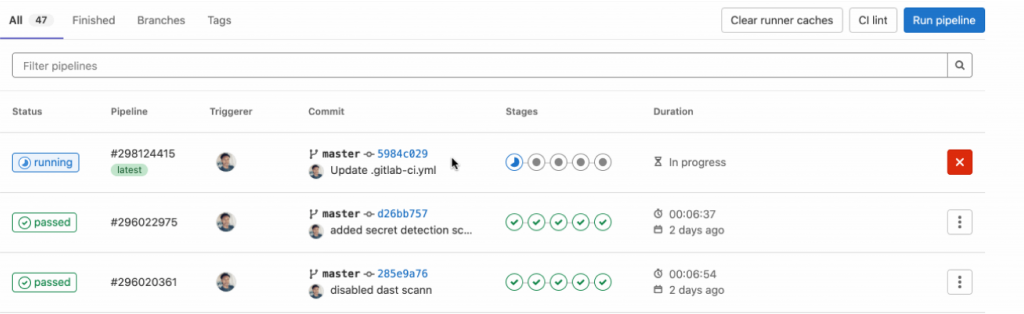
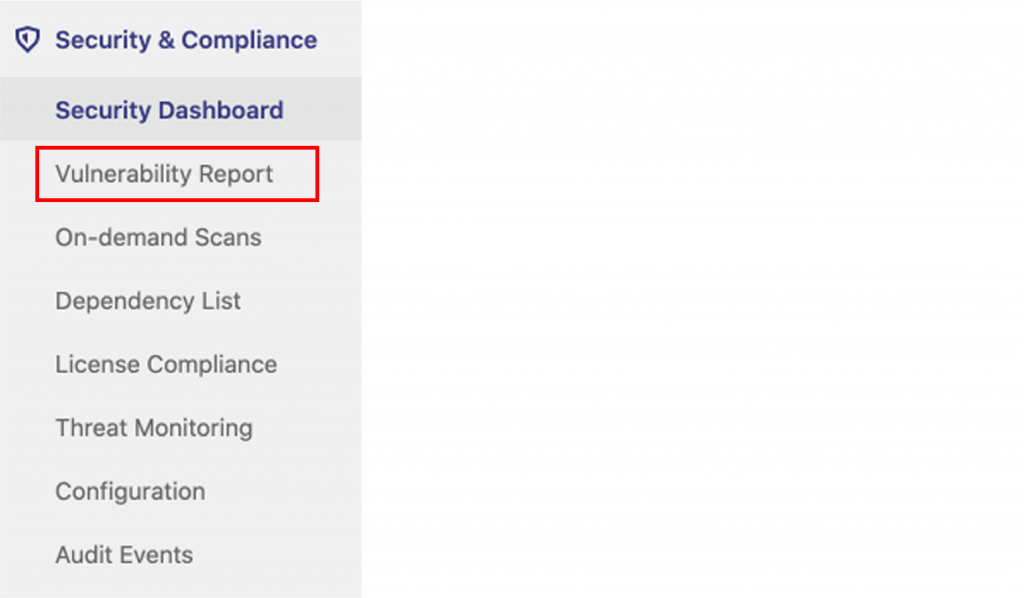
You can view the vulnerability report by clicking on Security & Compliance->Vulnerability Report
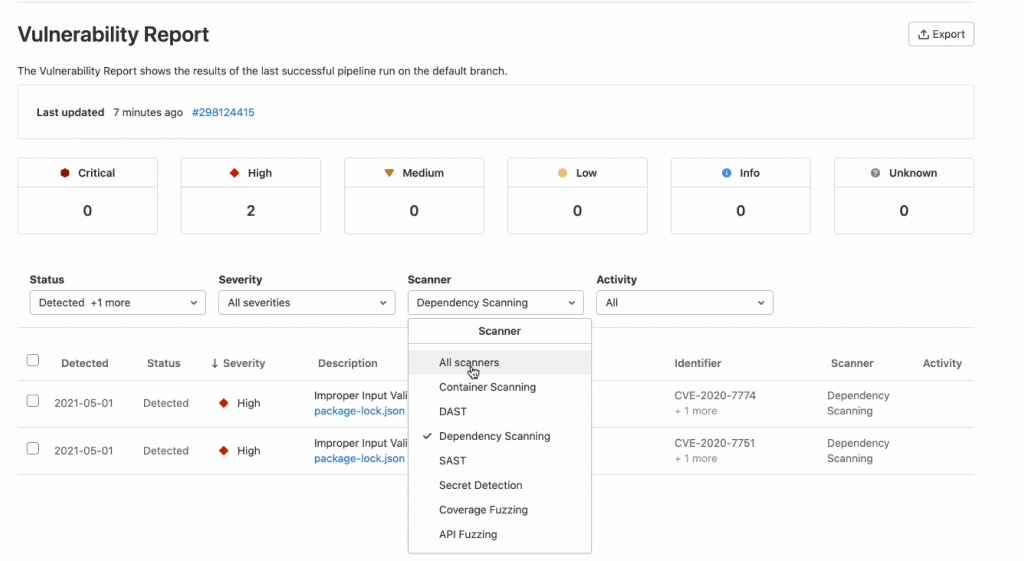
From here, you can keep improvising your app’s security by updating the node js, other docker container package dependencies and modifying your Docker file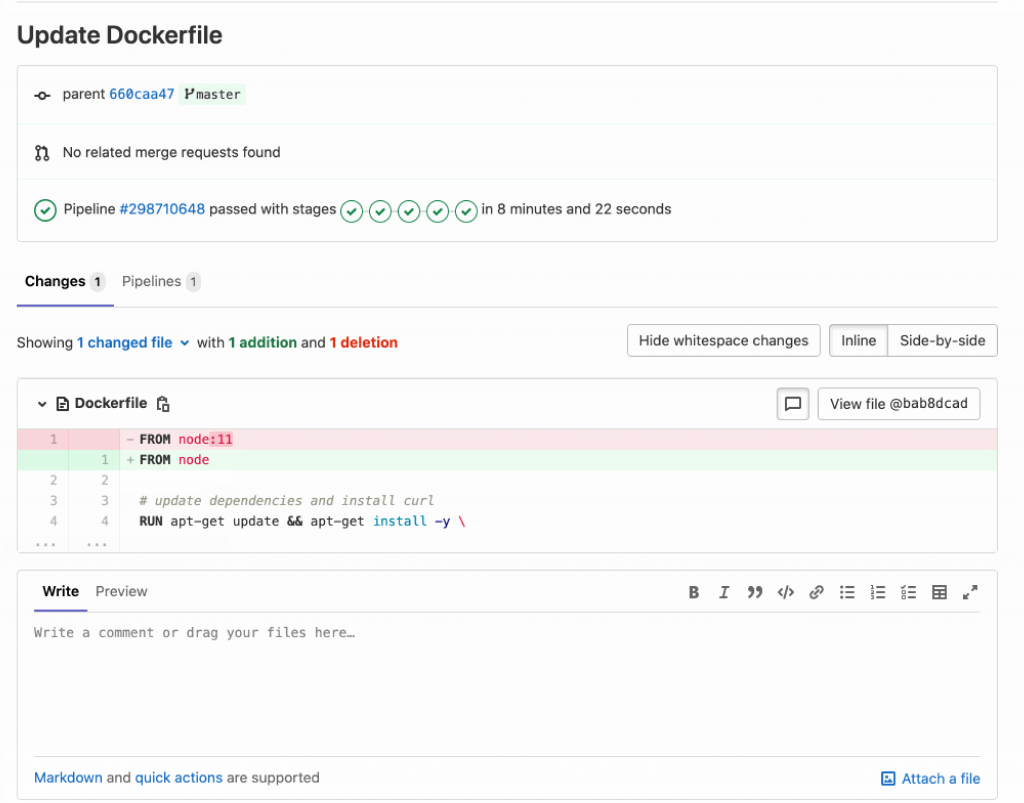
Parting Words
Overall, with DevSecOps available throughout the CI/CD workflow, a single application will help companies improve how they deliver code, reduce release cycles, and innovate. GitLab Secure is a DevSecOps game-changer that applies to governance, construction, verification, and deployment.








